Managed It Services - An Overview
Wiki Article
Some Ideas on Managed It Services You Need To Know
Table of ContentsFascination About Managed It Services For Law FirmsThe 4-Minute Rule for Managed It ServicesThe Only Guide to Managed It Services For Law FirmsSome Known Details About It Services Melbourne
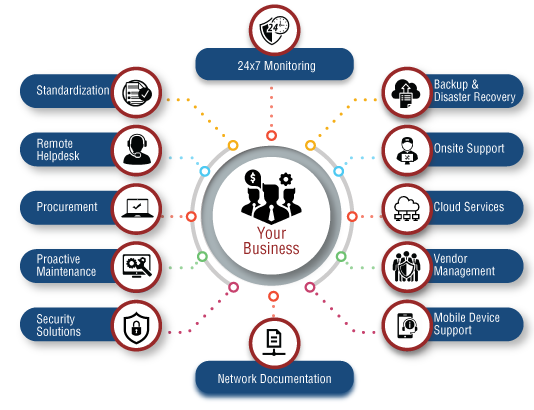
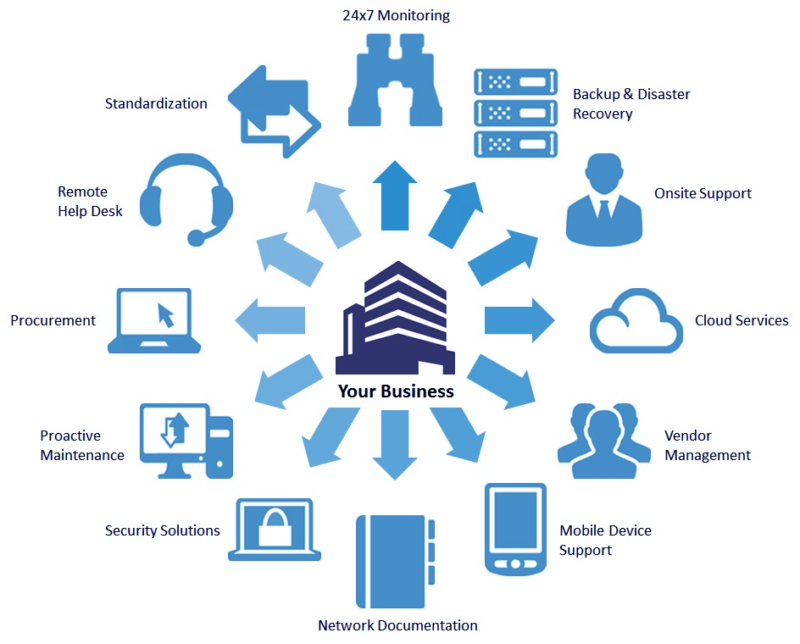
As foresaid, IT sustain offers end-to-end managed IT services, which include these mainly: An IT facilities has a number of laptop computers, workstations, printers, web servers and also hardware systems. A little damages or breakdown might wind up in a wonderful loss, which can be of vital data or details. This taking place ultimately effect on the company's returns and also connection.These policies have multi-factor authentication, stopping out of the state logins as well as many various other ones in a fantastic duty. This is incredibly for the business that permit workers to utilize their very own phones for performing tasks. This bring-your-own-device (BYOD) is not every usual, however still exists. The assistance offering business put their group to safeguard that data and properties from hackers or misuse.
It ensures that just safe tools will certainly have the ability to carry out remotely, as they would be qualified of safeguarding the delicate information of the business. It refers to the on-demand accessibility of computer system resources, including information storage space and computer power. This taking place does not need any direct energetic monitoring by the user.
As its benefits are fantastic, extra as well as more business have actually started shifting to the cloud for hosting their data. it services melbourne. For keeping their confidential details concerning customers as well as their client experience (CX) secure, it includes some outstanding protection functions. The technology support group manages it well in 2 methods: Making sure configuring and taking care of the cloud system for organizing a number of requisite applications, data administration, IT support and also downtime, Using the full safety and security to what comes under the handled IT solutions from cyber criminals.
The Single Strategy To Use For It Services Melbourne
Something went wrong. Wait a minute and also attempt once more Attempt once more.
Services are significantly relocating their IT infrastructures into the cloud (managed it services melbourne). Lots of venture organizations currently operate in multi-cloud atmospheres or make use of hybrid on-premises as well as it services melbourne cloud-based IT styles. These complexities demand the need for IT sustain services to manage these systems. Cloud computing assistance is an IT service that aids organizations manage their cloud-based facilities.
The 9-Minute Rule for It Services Melbourne
Includes screening information healing solutions to guarantee that they are trustworthy as well as efficient in the event of a data loss or corruption. IT sustain is necessary for businesses that depend greatly on their information, such as those in the medical care as well as financing industries.Workplace technology transforms rapidly and gets extra complicated by the year. Whereas the bulk of occupational computer as soon as occurred within the office wall surfaces and also inside a safe perimeter, today's dispersed labor force carries out business from houses, cafe, cars actually anywhere with internet gain access to. Supporting and protecting the myriad devices as well as access factors workers currently depend on to remain effective has actually developed a great deal even more help IT groups that often are currently spread out too thin.
Organizations look to taken care of companies (MSPs) for a selection of reasons, yet most generally, they are employed by organizations without any internal IT team or those that intend to utilize their in-house IT experts to focus on specific efforts instead of functional duties for taking care of innovation. MSPs provide a vast series of solutions from the basics such as assistance workdesk support and also keeping IT tools and also solutions operating all the method as much as giving the full suite of IT abilities, consisting of cyber safety, web connectivity, application assistance, data backups, as well as calamity healing.

The 7-Minute Rule for It Services Melbourne
Handled IT services are much from one-size-fits-all, so partnering with an MSP who understands your company as well as is actively bought assisting you meet your goals is essential.Prospective risks outside the network are protected against, ensuring that an organization's sensitive information remains inside. Organizations can go additionally by defining additional interior borders within their network, which can give enhanced protection and gain access to control. Accessibility control defines individuals or groups and the gadgets that have accessibility to network applications and also systems consequently refuting unauthorized access, as well as maybe hazards.
A susceptability is a fancy instance in a software system and a manipulate is an assault that leverages that vulnerability to acquire control of that system. When a manipulate is introduced, there is frequently a window of chance for assaulters to exploit that susceptability prior to the safety spot is applied.
Sandboxing is a cybersecurity practice where you run code or open documents in a secure, isolated atmosphere on a host equipment that mimics end-user operating atmospheres. Sandboxing observes the data or code as they are opened up and looks for malicious behavior to avoid risks from hopping on the network. Malware in files such as PDF, Microsoft Word, Excel as well as Power, Factor can be securely detected and blocked prior to the documents get to an unwary end individual.
Report this wiki page